In 2019, an estimated 1.94 billion people purchased goods or services online – and that number is growing year-on-year. However, those shopping online must be wary when making any online purchases, as our latest research has found that £36,262,000 has... Read More
News and Research
Specops supports PingID to secure password resets
Stockholm, November 17, 2020 – Specops Software released an update to its Specops Authentication platform today. The platform secures password resets, password changes, and encryption key recovery with multi-factor authentication (MFA). The introduction of PingID authentication advances security for... Read More
The holidays most likely to be found in your passwords [new data]
STOCKHOLM – Holidays are often a joyous time of year and new data seems to indicate people like to celebrate with their passwords. Today, Specops Software released an update to the Breached Password Protection list and a recent analysis... Read More
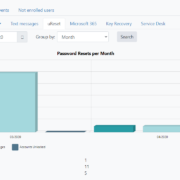
How to audit password changes in AD
Windows Server provides native tools for changing user passwords and auditing password changes in AD. However, they are somewhat lacking. Third-party tools such as Specops uReset can make the process easier and more secure. ADUC There are two main... Read More
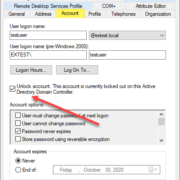
How to unlock active directory account lockouts
There is no question that one of the most common tasks that helpdesk and IT admins carry out on a daily basis is user account management. Specifically, triaging user account issues like unlocking active directory accounts in an Active... Read More
The most searched for programming languages around the world
As the employment market becomes more competitive, self-taught skills and experience have become increasingly valuable across the globe, and programming languages are no exception. In fact, our latest research found that thousands of individuals are looking to teach themselves... Read More
Understanding the Cybersecurity Maturity Model Certification (CMMC)
Long-standing information security best practices, frameworks, and regulations are a reliable means for ensuring that networks are resilient, and information remains secure. Still, oftentimes organizations and individuals will have their own interpretation of such security practices but that may... Read More
The most desired skills and qualifications for cyber security jobs, 2020
Cyber-attacks are becoming more and more prevalent, with some sectors being targeted more than others due to a lack of cyber security training. Thus, to neutralize risk and protect businesses from being compromised by cyber-attack threats, companies are beginning... Read More
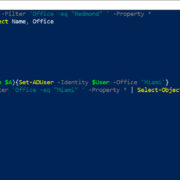
How to bulk modify Active Directory user attributes
Active Directory attributes often contain a wealth of information about users, including their phone numbers, department, location, and much more. Even so, this information is only valid if it is kept up-to-date. Sometimes this means updating an individual attribute,... Read More
Five useful tips on improving password security in your organization
Password-related breaches are on the list of the most popular attacks along with malware infection and social engineering. According to Verizon, almost 80% of all the breaches are connected with compromised credentials or weak passwords. While it’s a generally... Read More