IT departments have always invested heavily in making sure that their systems are able to positively confirm user identities prior to granting users access to sensitive resources. Not surprisingly, there are any number of mechanisms available for authenticating users.... Read More
Blog
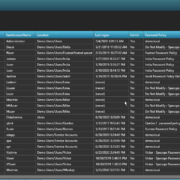
How to find default passwords in Active Directory
What causes identical or default passwords in Active Directory, and how can you find them? A lot of organizations script the creation of new user accounts to standardize, simplify, and speed up the process. Unfortunately, this can also leave... Read More
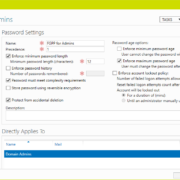
How to manage Active Directory password requirements
Password policies are a foundational element of any organization’s security posture, especially in environments managed by Active Directory (AD). These policies help ensure that user credentials meet baseline complexity requirements, reducing the risk of unauthorized access. However, understanding and... Read More
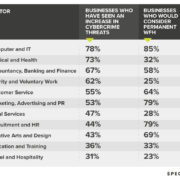
The Sectors Experiencing the Most Cyber-Attack Threats While Working from Home, Revealed
Which sectors are experiencing the largest number of cybercrime threats whilst working from home? To do this, we analysed 2,043 different businesses to find out which sectors are most “at risk.” Read More
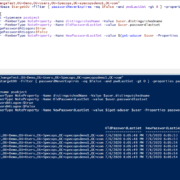
Resetting the clock on Active Directory password expiration
I recently worked with a customer who was implementing Specops Password Policy with Length-Based password aging. Usually we see customers use this to extend their maximum password age, for example: the current Active Directory maximum password age is 90 days;... Read More
The countries experiencing the most ‘significant’ cyber-attacks
Over the last decade, cyber security has rapidly become a concerning problem. Rightfully so, given how a cyber-attack can compromise an organisation’s key functions and processes within a matter of seconds, exposing sensitive data to opportunistic criminals. The impact... Read More
What’s Your Score? New Executive Summary Reports Available in Specops Password Auditor
Today’s release of Specops Password Auditor makes it easier for you to get sign-off on your password security project. “The IT admins we talk to understand the need for fixing the password vulnerabilities in their Active Directory environments,” said... Read More
How to get decision makers to sign-off on your password security project
While IT administrators often innately understand the cost of not addressing a cybersecurity project, it can be hard to get non-IT management to understand why certain projects should be prioritized. In their July 2018 survey, Spiceworks and AT&T found... Read More
Device encryption and compliance
Most companies want to protect data at rest on devices that are susceptible to theft. This will ensure that the data is inaccessible even if the hard drive is removed and replaced in another machine. Yet, lost and stolen... Read More
Common mistakes with endpoint encryption
Endpoint encryption is one of the cornerstones to securing data but it can introduce new challenges which can result in costly mistakes. Encryption is the process of changing information to make it unreadable without a proper authentication key. Administrators... Read More