How Microsoft Entra Password Protection works
Microsoft Entra (Azure AD) Password Protection comes included in P1/P2 Entra ID (Azure AD) plans. The name indicates users are protected from using bad passwords but that’s not the case. If an organization is serious about securing its Active Directory environment, whether on-prem or in the cloud, Entra ID built-in protections are not enough.
Microsoft Entra Password Protection includes two lists that it uses to check your users’ passwords against. Both are lacking, for different reasons.
The Global Banned Password List
Microsoft’s password scoring method: ”5 wrongs make a right”
“Even if a user’s password contains a banned password, the password may still be accepted if the overall password is strong enough otherwise.”
Microsoft does not block the use of passwords found on its Global Banned Password List or a configured Custom Banned Password List. Instead, the use of a banned word is only one part of Microsoft’s acceptance formula.
To pass their password filter, an entry must score 5 points. The use of a banned word is worth one point but that alone does not ban a password.
Step 1: Normalization
First, the password entry is converted to all-lowercase. Microsoft states that common leetspeak character substitutions are also reversed; however, some common substitutions like €→e and 8→b are ignored.
With Character Substitution enabled, Specops Password Policy blocks common leetspeak characters including the following which Microsoft ignores.
4 = a; € = e; 6 = g; 7 = t; 8 = b; 9 = g; § = s
Step 2: Fuzzy match check
The normalized entry is checked against the banned lists for exact matches +/- 1 character difference.
Step 3: Substring match check
The normalized entry is also checked against the user’s first name, last name and tenant name; however, partial matches (Jeff for Jeffrey) are ignored.
Specops Password Policy can block the full or partial use of a user’s first or last name.
Step 4: Final scoring
If the normalized entry makes it past the previous checks, Microsoft gives it a score. One point is given for: each exact match to a word on the global banned list; each exact match to a word on the custom banned list; each remaining unique character.
Entries must pass all of the above checks and reach a score of 5 to be accepted.
Example scoring:
Micr0soft1! [microsoft] + [1] + [!] = 3 → Rejected
Micr0soft124! [microsoft] + [1] + [2] + [4] + [!] = 5 → Accepted
Meaning, Microsoft will accept passwords containing dictionary words and known leaked passwords.
The “Global Banned Password List” is not a list of leaked passwords and does not fulfill compliance recommendations for a password deny list.
Unlike Specops Breached Password Protection, the Global Banned Password List does not include third-party data like that of Have I Been Pwned or other known breached password lists. Microsoft instead relies solely on its own analysis of what passwords are being used in various Entra ID environments. Microsoft does not disclose any of the contents of its list.
Regulatory recommendations like that of NIST or NCSC include using a list of known breached passwords. Specops Breached Password Protection fulfills this recommendation.
Microsoft does not state the number of passwords on the list. They say it is small compared to other third-party lists but that with fuzzy matching it can block millions of password variations from their smaller banned list.
Specops Breached Password Protection Complete is a larger banned password list, currently at over 4 billion unique compromised passwords.
The Custom Banned Password List
This is Microsoft’s competitive offering to Specops Password Policy’s custom dictionary lists.
The Custom Banned Password List has a limit of 1000 words, and each entry must be at least 4 characters long.
Three letter combinations are common for many companies. This 4-character limitation means you can’t block:
- Short company names or acronyms (like IBM, DSW, CBS, FOX, CNN, UPS, CVS, ATT, 3M)
- Shorter stock symbols (like GE, BBD, GM, BMY)
- Airport codes (like JFK, LHR, LAX, CDG, DXB, ARN, YYZ, FRA)
- Internal abbreviations (like product short names: SPP, BPP, SSD)
Specops Password Policy dictionary lists have no limit and allow entries of any length.
Microsoft doesn’t always block the use of words from the Custom Banned Password List. Microsoft’s “5 Wrongs Make a Right” approach to password scoring means that a word on your custom list can be allowed as part of a longer password.
Weak passwords accepted by Azure AD
Specops124!
[specops] + [1] + [2] + [4] + [!] = 5 → Accepted
Password998!
[password] + [9] + [9] + [8] + [!] = 5 → Accepted
PasswordPasswordPasswordPassword9
[password] + [password] + [password] + [password] + [9] = 5 → Accepted
Specops Password Policy can block the use of any word on custom dictionary lists in a longer password.
Breached Passwords
The infamous password breaches, Collections leaks #1-5, contain over a billion compromised passwords. Microsoft ignores them along with other third-party and real attack data in its Global Banned Password List, leaving users vulnerable.
Below are just a few examples of the most common complex passwords found in Collection #2 that pass Microsoft’s Password Protection filter.
Leaked passwords accepted by Azure AD
FQRG7CS493
Sojdlg123aljg
D1lakiss
Indya123
The Specops Password Policy password deny list includes the above known breached passwords and over 4 billion more compromised passwords.
While recommending removing expiry, Microsoft Entra (Azure AD) Password Protection only checks for compromised passwords at reset or change.
“When users change or reset their passwords, these banned password lists are checked to enforce the use of strong passwords.”
Microsoft often strongly recommends getting rid of expiry, though we find most organizations are not ready for it. However, Microsoft Entra (Azure AD) Password Protection lacks any method for checking for compromised passwords outside of at change or reset. Fewer expiry events means that users covered by Microsoft Entra Password Protection have their password checked for compromise very infrequently.
Specops Password Policy offers continuous protection against the use of compromised passwords with a daily scan against the daily updated list as well as during password change.
More Than Security Gaps, User Experience is Lacking
Microsoft Entra Password Protection is likely to increase IT service desk calls.
“Microsoft Entra (Azure AD) Password Protection has no control over the specific error message displayed by the client machine when a weak password is rejected.”
Microsoft Entra Password Protection is likely to increase calls to the IT service desk for two main reasons.
This vague messaging is not likely to make it clear to the user what they need to change about their password in order to for it to be accepted.
With Specops Password Policy, users receive dynamic feedback at password change as they type. Specops also enables admins to customize the message that users receive, including displaying the found dictionary word.
#2 – The inherent complexity of Microsoft Entra (Azure AD) Password Protection scoring
The password scoring used in the Microsoft Entra Password Protection is complicated, and IT admin logs will tell you a password was rejected because it was found on the global or custom banned list but not tell you which.
This lack of transparency on rules for what is required means that the IT service desk will struggle to successfully identify issues users are having with setting passwords.
With Specops Password Policy, admin logs identify on which password list a rejected password entry was found.
What we recommend
You don’t need to abandon Entra ID to implement stronger password policies or to block users from using
compromised passwords.
You can instead set up Specops Password Policy and Breached Password Protection to enforce these policies in your on-prem environment and utilize a federation solution or Microsoft Entra (Azure AD) password write-back to enforce those policies for your users across environments.
Find out how many of your Entra ID (Azure AD) users’ passwords are
still compromised
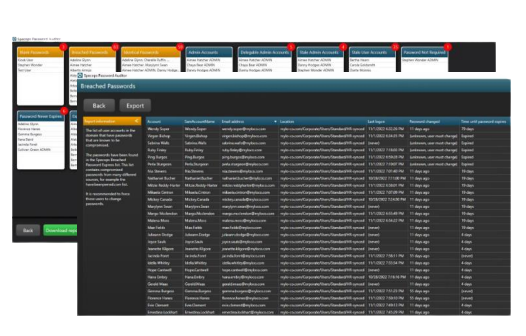
Specops Password Auditor is a free read-only
tool that scans and checks passwords of Active
Directory user accounts against our list of
compromised passwords.
Many of our customers who were relying only
on Microsoft Entra (Azure AD) Password Protection have told us
they were shocked to find how many compromised passwords were in use after running a Password Auditor scan.
It takes a single compromised password to create risk and potential compromise. Download your free copy of Specops Password Auditor here.
Get a demo of Specops Password Policy
Specops Password Policy helps increase password security in your on-prem Microsoft Active Directory or hybrid Entra ID (Azure AD) environment. The solution can target any GPO level, group, user, or computer with password complexity, dictionaries and passphrase settings. With Specops Breached Password Protection, IT teams can block over 4 billion unique compromised passwords. These passwords include ones used in real attacks today or are on known breached password lists, making it easy to comply with industry regulations such as those from NIST or NCSC.
Interested in seeing how Specops Password Policy and Breached Password Protection could work in your environment? Click here to set up a free demo or trial for our Active Directory Password Policy Protection tool today.